How to change your system MAC address (Spoof) to stay anonymous. How to attack any close wireless network and get all details about it (including target network MAC address, SSID, Encryption Type, etc). How to get the MAC addresses for all clients connected to the target network without even knowing the password of the target router. A Step By Step Tutorial On How To Change / Spoof Mac Address In Kali Linux 2020.1-For Beginners: -If. Your new MAC address will now show while listing network interface using ifconfig command: Change to a Specific MAC address The following procedure on Kali Linux can be used to spoof MAC address to a specific string.
- Hack With Mac Address Kali Password
- Hack With Mac Address Kali File
- Hack With Mac Address Kali Software
The idea behind a MAC flooding attack is to send a huge amount of ARP replies to a switch, thereby overloading the cam table of the switch. Once the switch overloads, it goes into hub mode, meaning that it will forward the traffic to every single computer on the network. All the attacker needs to do now is run a sniffer to capture all the traffic.
This attack does not work on every switch; lots of newer switches have built-in protection against an attack.
Hack With Mac Address Kali Password
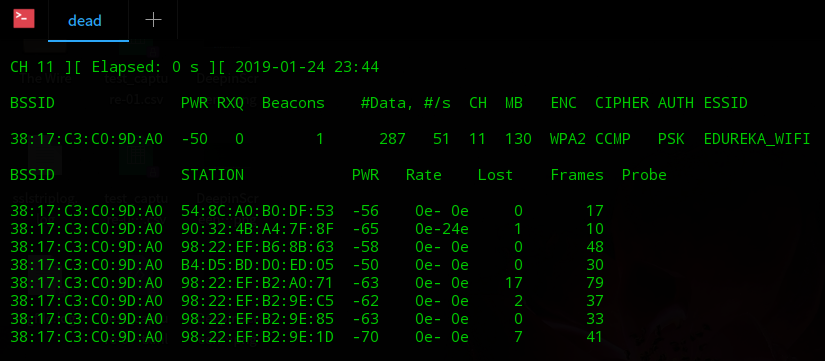
Kali btscanner. Then select “i” to initiate an inquiry scan. You can see the results below. Using btscanner, we can get a list of all the Bluetooth devices in range. This one here has a MAC address and a name of “Tyler”—to spoof this device, we must spoof the MAC address and name of the device.
Macof
Macof fills the cam table in less than a minute or so, since it sends a huge number of MAC entries approx 155,000 per minute, to be specific.
The usage is extremely simple. All we need to do is execute “macof” command from our terminal. This tool is already installed in all Kali Linux versions.
Once the cam table has been flooded, we can open Wireshark and start capturing the traffic. By default, Wireshark is set to capture the traffic in the promiscuous mode; however, you don’t need to sniff in the promiscuous mode when a switch goes into a hub mode since the traffic is already promiscuous.
But in ARP Poisoning, the ARP protocol would always trust that the reply is coming from the right device. Due to this flaw in its design, it can in no way verify that the ARP reply was sent from the correct device. The way it works is that the attacker would send a spoofed ARP reply to any computer on a network to make it believe that a certain IP is associated with a certain MAC address, thereby poisoning its ARP cache that keeps track of IP to MAC addresses.
So these two attacks i.e. ARP Poisoning and Mac Flooding, both are associated with ARP Protocol.
To view more about macof, just type “macof -h” which shows you all best possible options.

Usage: macof [-s src] [-d dst] [-e tha] [-x sport] [-y dport] [-i interface] [-n times]
Where,
- -i interface Specify the interface to send on.
- -s src Specify source IP address.
- -d dst Specify destination IP address.
- -e tha Specify target hardware address.
- -x sport Specify TCP source port.
- -y dport Specify TCP destination port.
- -n times Specify the number of packets to send.
For Simple Flooding, the command is “macof -i eth0 -n 10”
Hack With Mac Address Kali File
For Targeted Flooding, the command is “macof -i eth0 -n 10 -d 192.168.220.140”
Some of the major countermeasures against MAC Flooding are:
Hack With Mac Address Kali Software
- Port Security – Limits the no of MAC addresses connecting to a single port on the Switch.
- Implementation of 802.1X – Allows packet filtering rules issued by a centralised AAA server based on dynamic learning of clients.
- MAC Filtering – Limits the no of MAC addresses to a certain extent.
